Digital Marketing
How to Outsource PHP Programming Services

Outsourcing PHP programming services has become a popular trend among businesses that want to develop web-based applications or websites. Outsourcing PHP programming services can help companies reduce their costs and improve their productivity by tapping into the expertise of PHP developers. However, outsourcing PHP programming services requires careful planning and execution to ensure success. In this article, we will discuss how to outsource PHP programming service.
Identify Your Requirements(How to Outsource PHP Programming Services)
The first step to outsourcing PHP programming services is to identify your requirements. You need to know what you want to achieve with the PHP programming service you are outsourcing. You should also know the functionalities that you want in your web-based application or website. Having a clear understanding of your requirements will help you identify the skills and expertise you need in a PHP developer.
Search for the Right PHP Development Company
Once you have identified your requirements, the next step is to search for the right PHP development company. You can search for PHP development companies online, check their portfolios, read their reviews, and compare their rates. Look for PHP development companies that have experience in developing web-based applications or websites similar to yours.
Evaluate the PHP Development Company
After finding PHP development companies that match your requirements, evaluate them. Check their experience, expertise, and technical skills. You can also ask for references and contact their previous clients to know their experience working with the PHP development company. You should also check the communication skills of the PHP development company. Communication is crucial when outsourcing PHP programming services. You should be able to communicate effectively with the PHP development company to ensure that they understand your requirements and deliver the project on time.
Discuss the Project Scope and Timeline(How to Outsource PHP Programming Services)
Once you have evaluated the PHP development company and are satisfied with its expertise, you should discuss the project scope and timeline. Clearly define your project requirements and discuss them with the PHP development company. You should also discuss the timeline for the project, including milestones, deadlines, and deliverables. This will help you ensure that the PHP development company delivers the project on time and within budget.
Sign a Contract
After finalizing the project scope, timeline, and budget, sign a contract with the PHP development company. The contract should clearly define the scope of the project, timeline, budget, payment terms, and project milestones. The contract should also include a confidentiality agreement to protect your intellectual property rights.
Monitor Progress
Once the PHP development company starts working on your project, monitor the progress regularly. You can use project management tools such as Trello, Asana, or Jira to track the progress of the project. Regular communication with the PHP development company is also crucial to ensure that the project is on track.
Test and Deployment(How to Outsource PHP Programming Services)
After the PHP development company has completed the project, test the web-based application or website thoroughly. You should test the web-based application or website on different devices, browsers, and platforms. Once you are satisfied with the testing results, deploy the web-based application or website to your server.
Conclusion
Outsourcing PHP programming services can help businesses reduce costs and improve productivity. However, outsourcing PHP programming services requires careful planning and execution. By following the steps mentioned above, you can outsource PHP programming service successfully. Identify your requirements, search for the right PHP development company, evaluate the PHP development company, discuss the project scope and timeline, sign a contract, monitor progress, and test and deploy the web-based application or website.
Digital Marketing
How to calculate CPM in digital marketing?
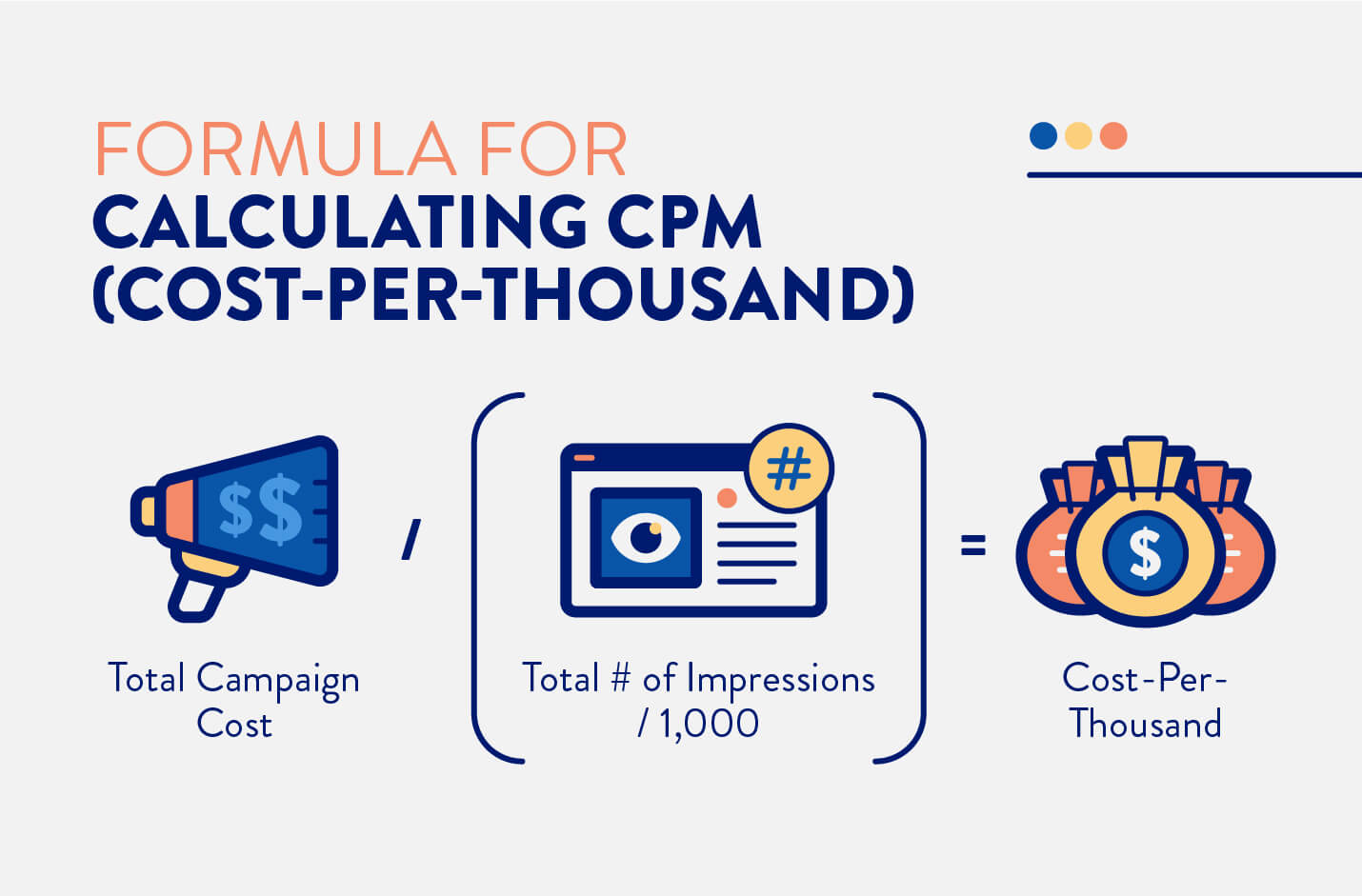
.CPM in digital marketing: When it comes to digital marketing, there are a lot of acronyms and terms that can be confusing. CPM is one of them. What does CPM stand for, and more importantly, how can you calculate it? In this post, we’ll break it down so you can understand what CPM is and how to calculate it in your own marketing campaigns. Stay tuned!
What is CPM and How to Calculate It?
CPM stands for cost per mile or cost per thousand impressions. In other words, it’s a way to measure how much it costs you to reach 1,000 people with your marketing message.
To calculate CPM, simply divide your total ad spend by the number of impressions your ad received. For example, if you spent $100 on an ad campaign that received 10,000 impressions, your CPM would be $10.
It’s important to note that CPM is just one of many ways to measure the success of a digital marketing campaign. Other common metrics include cost per click (CPC) and cost per conversion (CPA).
Ultimately, the metric you should focus on depends on your goals for the campaign. If you’re trying to generate leads, CPC might be more important than CPM.
However, if you’re just trying to raise brand awareness, CPM could be a better metric to track.
An important thing to know:
Ad impressions and page views are two concepts that are often confused. An ad impression is defined as a single instance of an ad being displayed, regardless of whether it is clicked on or not. In contrast, a page view is counted every time a visitor loads a web page.
So, if an ad is displayed twice on the same page, that would count as two impressions but only a one-page view. It’s important to understand the difference between these two metrics because they can have a big impact on your advertising budget.
If you’re paying for ad impressions, you may end up spending more money than you need to if your ad is displayed multiple times on the same page. On the other hand, if you’re paying for page views, you may miss out on potential customers if they don’t scroll down far enough to see your ad.
Therefore, it’s important to choose the pricing model that makes the most sense for your business goals.
Examples of how to use CPM in digital marketing campaigns:
- Facebook advertising:
When you create a Facebook ad, you have the option to pay per click (CPC) or per thousand impressions (CPM).
- Google AdWords:
Google AdWords also offers CPC and CPM options for your ads.
- Display advertising:
Display advertising is another form of online advertising that can be purchased on a CPM basis.
- Native advertising:
Many native advertising platforms, such as Taboola and Outbrain, charge advertisers on a CPM basis.
8 Tips for reducing your CPM:
- Target your audience:
The more targeted your audience, the less money you’ll have to spend to reach them. For example, if you’re trying to reach people in a specific city, you can target your ads to people who live in that city. Or, if you’re selling a product for women, you can target your ads to women only.
- Use retargeting:
Retargeting is a technique that allows you to show your ads to people who have already visited your website. This is a great way to reach people who are already interested in your product or service.
- Use relevant keywords:
When it comes to digital marketing, using the right keywords is essential for reaching your target audience. By targeting relevant keywords, you can reduce your CPM and reach more potential customers.
For example, if you’re a small business that sells women’s clothing, you could target the following keywords:
a -Women’s clothes
b -Women’s Fashion
c -Women’s clothing online
d -Clothing for women
These are just a few examples of relevant keywords that you could use in your digital marketing campaigns. To find more relevant keywords, use a tool like Google AdWords Keyword Planner.
CPM in digital marketing
- Use social media:
Social media platforms such as Facebook and Twitter offer great targeting options that allow you to reach very specific audiences. Make sure to take advantage of these options to get the most out of your advertising budget.
- Test different ad formats:
Not all ad formats work the same for everyone. Try out a few different types of ads and see which ones produce the best results.
- Optimize your website:
Make sure your website is optimized for maximum conversion potential. If people don’t buy anything when they visit your site, they’re not going to be interested in buying anything when they see your ads.”
- Test different ad formats:
Some ad formats are more expensive than others. By testing different formats, you can find the one that gives you the most bang for your buck.
- Try a different pricing model:
If you’re not happy with your CPM, try a different pricing model. For example, if you’re paying per click, you may want to try paying per impression.
Conclusion:
CPM is a useful metric for measuring the success of digital marketing campaigns, but it’s just one of many options. The most important thing is to choose the metric that makes the most sense for your business goals. Now that you know how to calculate CPM, you can start using it to measure the success of your digital marketing campaigns. Just remember to keep your goals in mind, and don’t get too bogged down in the numbers. At the end of the day, it’s all about getting results!
Digital Marketing
The Ultimate Guide to YouTube Downloaders: A Convenient Way to Save Videos

Ultimate Guide to YouTube Downloaders. YouTube has developed into a goldmine of amusing and educational video in the current digital era. However, there are situations when you might wish to archive your favorite films for later use or save them for offline playback. Downloaders for YouTube might be useful in this situation. This in-depth tutorial will examine the advantages of YouTube downloaders and offer a list of excellent choices to improve your downloading experience.
Understanding YouTube Downloaders
Users can download YouTube videos to their devices using tools or software known as YouTube downloaders. By removing the video and audio files from the YouTube site, these tools allow users to store them locally. You may access your favorite YouTube videos offline, get around sluggish internet connections, and enjoy uninterrupted playback using a YouTube downloader.
Benefits of Using YouTube Downloaders
Offline viewing and Convenience
The comfort of watching videos offline, whenever you want, is made possible by YouTube downloaders. These apps let you watch material without relying on an internet connection, whether you’re travelling, in a place with poor service, or just want to save a movie for later.
2.2 Reference and Archiving
You may wish to refer back to several YouTube videos’ essential content in the future. You may build a personal library of information by downloading and storing these movies, ensuring that you always have quick access to the information you value the most.
2.3 Control and Quality
You may frequently choose the video quality and format you want with YouTube downloaders. This enables you to modify the video to suit your particular requirements, whether you want to maintain the best definition or reduce the file size to free up storage space.
Top YouTube Downloaders
3.1 Downloader for 4K videos
A well-liked option among customers is 4K Video Downloader, which is renowned for its simplicity and adaptability. It enables downloading videos in a range of qualities and formats, including 360-degree and 4K films. Users may also extract audio tracks from movies using this tool.
3.2 Download videos with Freemake
The feature-rich programmed Freemake Video Downloader enables downloading videos from YouTube as well as other sites. Its user-friendly interface makes it perfect for downloading many videos at once, and batch downloads are supported. The programmed also allows for the format conversion of videos.
Video Downloader 3.3 YTD
YTD Video Downloader is renowned for its dependability and quickness. It has an easy-to-use interface and enables users to download movies in a variety of formats and resolutions. A built-in video player allows you to preview downloaded content and is included with the programmed.
ClipGrab 3.4
Windows, macOS, and Linux users may download YouTube videos using ClipGrab, a free and open-source programmed. It has a straightforward user interface and enables downloading videos in several file formats. Additionally, ClipGrab offers the possibility to concurrently download videos and extract audio.
Conclusion
For anybody who wishes to save YouTube videos for offline watching, preservation, or reference. Ultimate Guide to YouTube downloaders are a priceless resource. They let you to watch your favorite material even when there is no internet connection, manage the visual quality, and with convenience. In this post, we looked at some of the best YouTube downloaders, as well as the advantages of utilizing them. You can improve your video viewing experience and take full use of YouTube’s extensive content catalogue by using the best YouTube downloader available.
Digital Marketing
LiteBlue: A Comprehensive Guide to USPS Employee Services

The United States Postal Service (USPS) uses technology to improve employee satisfaction and streamline operations in the current digital era. LiteBlue stands out among the many advancements as a potent web portal that provides access to USPS services for employees. USPS employees have access to an extensive selection of resources and tools through LiteBlue, from accessing personal records to staying up to date on business news. In this thorough overview, we’ll examine LiteBlue’s many features and emphasize how important they are for improving the USPS employee experience.
1. What is Lite Blue?
A secure web portal created particularly for USPS employees is called LiteBlue. It provides a range of services to meet the needs of postal employees, providing effective communication, easy access to information relating to their jobs, and practical self-service features.
2. The Benefits of LiteBlue
Employees at USPS can benefit from LiteBlue in a number of ways, including:
a) Online Self-Service: Using LiteBlue, employees can examine their work schedules, access personal information, request time off, and modify their direct deposit information. This simplified self-service method helps users save time and effort.
b) PostalEase: LiteBlue’s PostalEase function enables employees to control and modify their health benefits throughout open enrollment periods. With the help of this simple tool, employees may tailor their benefits to meet their specific needs.
c) professional Development: LiteBlue gives staff members useful information about chances for professional progression at USPS. This promotes loyalty among the staff and supports professional development.
d) staff Recognition Programmes: LiteBlue sponsors a number of staff recognition programs to recognize exceptional performance and commitment. Such praise raises spirits and encourages workers to give their best work.
e) Communication Channel: USPS makes use of LiteBlue as a platform to inform staff members of important information, updates, and policies. By doing this, it is made sure that employees are informed about organizational advancements.
3. How to Access LiteBlue
Employees of USPS must register for a LiteBlue account in order to access Lite Blue. The first steps are as follows:
a) Registration: By going to the official USPS Lite Blue website, employees can sign up for LiteBlue. To finish the registration procedure, they will require their employee identification code (EIN) and other pertinent information.
b) Logging In: After registering, employees can access LiteBlue by entering their special EIN and a password of their choosing. The portal uses strong security measures to safeguard user information.
4. LiteBlue Features in Detail
a)Employees can view and edit their personal information in Lite Blue, including contact information and emergency contacts. As a result, USPS will always have correct and current employment records.
b) Work Schedule: The portal shows the work schedules of the employees, allowing them to easily plan their personal obligations. Employees can also review their booked vacation time and seek changes if necessary.
c)LiteBlue provides access to payroll information, such as pay stubs, earnings, and deductions. This openness improves confidence and decreases questions about payroll.
d) eOPF (Electronic Formal Personnel Folder): The eOPF feature is provided by LiteBlue and allows users to access and manage their company’s official personnel data. This electronic method reduces the possibility of losing important documents and saves time.
e) PostalEase Benefits: As was already indicated, PostalEase offers online health benefits management for employees. During open enrollment periods, they can go over the choices, decide what they want, and adjust their coverage.
f)LiteBlue provides tools to discover career development opportunities, including job ads, training courses, and advice on career growth.
g) Employee Comments: USPS appreciates employee comments. Employees can anonymously share their ideas, report problems, and make suggestions with Lite Blue. This open line of communication promotes ongoing development and fosters a supportive work atmosphere.
Conclusion
In conclusion, LiteBlue significantly improves the working environment for USPS employees. LiteBlue is a useful tool that improves operations and promotes employee happiness since it offers simple access to personal information, facilitates smooth communication, and offers opportunities for career growth. The fact that USPS embraces technology through tools like Lite Blue demonstrates its dedication to both innovation and worker well-being in the twenty-first century. LiteBlue will definitely continue to be a crucial component of USPS’ personnel management strategy as it develops further.
-

 Fashion6 months ago
Fashion6 months agoHow To Style Earrings for a Night Out
-

 Real Estate1 year ago
Real Estate1 year agoHow to Unlock the Benefits of Real Estate Investment in Pakistan
-

 Tech11 months ago
Tech11 months agoTMIIS Virtual Gateway: Opening New Horizons in Global Connectivity
-

 Business2 months ago
Business2 months agoWhat Can You Expect from a High-End London Office Space?
-

 Digital Marketing2 months ago
Digital Marketing2 months agoHow to calculate CPM in digital marketing?
-

 Lifestyle12 months ago
Lifestyle12 months agoThe New Trend in Home Furnishings Teapoy and Wooden Sitting Stool
-

 Digital Marketing6 months ago
Digital Marketing6 months agoA Step-by-Step Guide To Become A Cyber Security Architect
-

 General2 months ago
General2 months agoUnraveling the Mysteries of “λιβαισ”: A Comprehensive Guide
